
Video Meeting Privacy and Security | Secure Video Conferencing with RingPlan Meet™
Developing a platform that will provide value to video conferencing users is very important to us. Privacy and security play a critical role in providing value to today's consumers; a responsibility we take very seriously.
![]() Certainly more than a simple business phone system, RingPlan now provides our customers access to an unlimited, fully-secure meeting space that leaves no digital fingerprints.
Certainly more than a simple business phone system, RingPlan now provides our customers access to an unlimited, fully-secure meeting space that leaves no digital fingerprints.
This video conferencing platform is called RingPlan Meet.
Interested in a demo, email demos@ringplan.com.
What Does Fully Secure Video Conferencing Mean?
RingPlan Meet gives users the option to leave no digital fingerprints. Meetings can be private and these meetings expire once they are done taking place.
One-time meetings are created when an individual initiates a meeting and the meeting is deleted once the last person leaves.
These Are Disposable Meeting Links
Unless purposefully creating a recurring meeting, rejoining the same room after the meeting has expired initiates a new meeting, deleting any connection to the previous meeting even if the meetings have the same name.
Ensuring one-time meetings expire immediately helps keep your communications secure.
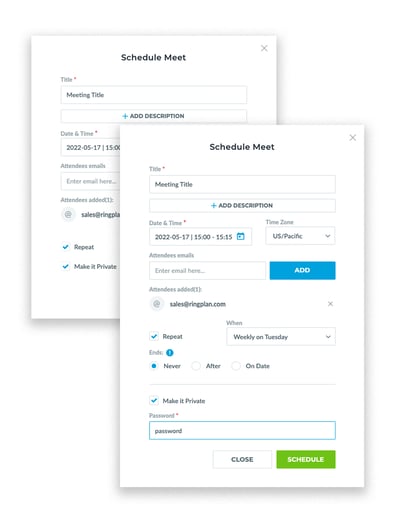 Recurring Video Conference Meetings
Recurring Video Conference Meetings
Users can create a recurring meeting by scheduling a meeting using their RingPlan Meet dashboard located at my.ringplan.com/apps/.
RingPlan will take care of sending a calendar invite to your guests with the meeting details, including date, time, and meeting URL.
Video Conferencing Privacy and Security
Although users have the option to create 'disposable' one-time links, one still has to be careful about where meeting links are shared and published to prevent targeted mischief.
One can prevent such problems by setting a meeting password and sharing this password with attendees only.
Passwords expire at the end of a meeting when the last person leaves the room, or when the host is the only person in the room and exits.
Anyone Can Mute or Remove You from a Meeting
For your security and privacy, RingPlan Meet deployed soft moderation controls. We decentralize meeting moderation.
 Moderation controls serve to help address technical issues that arise in video meetings. Often, users do not realize they are experiencing connectivity issues; that their microphones are noisy, or that they have left their camera running.
Moderation controls serve to help address technical issues that arise in video meetings. Often, users do not realize they are experiencing connectivity issues; that their microphones are noisy, or that they have left their camera running.
Opening moderation control to everyone in the meeting helps a meeting proceed with minimal interruption to the presenter, and reduces your exposure to such risks.
Rather than one individual responsible for both the presentation and technical issues. Others in the meeting can utilize these soft controls to mediate the technical issues, leaving the presentation uninterrupted.
RingPlan Meet Supports End-to-End Encryption
Turn on end-to-end encryption (e2ee) during any meeting, on any browser that supports insertable streams.
Users can turn on e2ee by selecting the ‘End-to-End Encryption’ option in the overflow menu during any meeting. Attendees of e2ee meetings will need to make sure they enter the exact same password in the Key field.
Browsers that support insertable streams, based on Chromium 83 and above can support end-to-end encryption. This includes Microsoft Edge, Google Chrome, Brave, and Opera.
Even without end-to-end encryption, RingPlan Meet security remains strong
Meetings operate in 2 ways: Peer-to-Peer (P2P) or Videobridge (RVB). P2P is used for 1-to-1 meetings, encrypted using DTLS-SRTP from sender to receiver.
Meetings with more people are also encrypted using DTLS-SRTP. This encryption is removed while traversing RingPlan Videobridge, but never stored or retained in memory while being routed. End-to-end encryption of packets can not be removed, this acts as a second layer of encryption on top of the DTLS-SRTP.
Why is Security Important to Us
Your Privacy and Security is important to us.
Over the years we have seen many examples of how privacy breaches can wreak havoc on businesses.
Our world is not the same as it once was. All of our important data is stored digitally. There are individuals who make a living by exploiting vulnerabilities in this digital system for fiscal gain.
Businesses must be quick to adapt to these threats to protect user data from exploitation.
RingPlan answer to the threat, in regards to video conferencing, is to provide encryption and password protection to meetings while decentralizing moderation control of all meetings to allow colleagues to assist each other protect their privacy.
Interested in a Video Demo?
Get a video demo of RingPlan Meet and all other features included in the RingPlan Business Phone System, including Hosted Phone, SMS Text Messaging from computer, Fax from computer, amongst others. Reach out to demos@ringplan.com to get started or fill out the form below.